If you are among the ever-increasing number of VPN users, you are probably familiar with IKEv2, a top protocol frequently offered by VPN companies. IKEv2 is an excellent solution for the best smartphone-based internet experience combined with IPSec.
Understanding IKEv2 allows you to make choices regarding your digital security. It might assist you in determining if you are a technologically aware individual or an IT expert. Continue reading to learn about IKEv2 and optimize your online experience. We’ll look at how the protocol works and its advantages and disadvantages.
What is IKEv2?

The IKEv2 is a VPN protocol that secures data transmissions between two devices via the web. It is a powerful combination of the IKEv2 key management and IPSec technologies. It is a standard option for setting up VPNs across different devices and OSs. IKEv2 has replaced the original IKE protocol.
The protocol offers a safe and dependable way to create and keep VPN tunnels. It uses the IPsec protocols, which secure data transmission between the VPN client and server. It further provides data encryption, data integrity checks, and authentication.
IKEv2 establishes a secure tunnel using both symmetric and asymmetric cryptography. Digital certificates or pre-shared keys verify the authentication of the client and server at the outset of IKEv2. Once authenticated, it determines encryption and integrity algorithms to ensure security.
Another remarkable feature of IKEv2 is its easy adaptation to changing networks. Its fast reconnection can help network switches and alterations. For example, it switches from Wi-Fi to cellular data connections within seconds. Therefore, IKeV2 is an excellent choice for mobile devices.
Why Do IKEv2 and IPsec Always Come Together?
Both IKEv2 and IPsec are merged together by the combined efforts of Microsoft and Cisco. This has been done particularly because of their speeds.
IKEv2 works on a surface level (in this case, the user space). Due to this, it can easily access and retrieve files already stored. This data is then used by the VPN protocol for a secure VPN connection.
On the contrary, IPsec runs from the Kernel, which is the deepest layer or core of an operating system. Thus, it is able to perform data processing at a significantly higher speed. Plus, IPsec provides necessary security functions for secure data transmission.
Here’s how they support each other. At first, the IKEv2 protocol collects a few data packets and creates a connection with the client server. Then, it takes all the data present in its directory—i.e, the IP addresses, ports utilized—and hands it over to IPsec, which then encrypts all the data.
IKEv2 and IPsec help each other in creating secure virtual private networks. Both work together in establishing the tunnel and enhancing compatibility. They also allow easy deployment of IKEv2 VPN solutions on various platforms and operating systems. This unification provides guaranteed secure connections between different VPN devices and software.

What’s the Difference Between IKEv1 and IKEv2?
The IKE protocol, used in VPNs, has two versions: IKEv1 and IKEv2. Though they both perform a similar task, they have various significant features. Let’s look at how both of these protocols differentiate:
Security
IKEv2 is a total upgrade of IKEv1 in terms of security. This is because the newer version has the latest security algorithms, like ChaCha20, AES, and Camellia. On the other hand, IKEv1 doesn’t have encryption keys that makes it less secure.
Speed
IKEv2 supports Network Address Translation-Traversal (NAT-T), which increases its speeds and functionality, making it on the better performance side compared to IKEv1. Plus, IKEV2 offers Mobility and Multi-homing protocol (MOBIKE). What does it actually do? Due to this, you can easily switch connections from mobile to Wifi and vice versa.
That’s not just all; IKEv2 consumes less data bandwidth as it seamlessly establishes the connection.
Reliability
IKEv2 is designed for seamless mobility and network transitions. It uses a single-phase negotiation rather than the ancient two-phase negotiations used by IKEv1.
Furthermore, IKEv2 is supported on various platforms and operating systems. For all these reasons, it is becoming the preferred choice for modern VPN deployments.
Is IKEv2 VPN Safe?
Yes, the VPN protocol is safe to use, as explained by many cryptographic experts. IKEv2 utilizes strong security features, which include encryption algorithms such as AES 256. Plus, it makes sure that only authorized devices can establish a secure connection.
For this, the protocol uses several authentication methods (digital certificates, pre-shared keys) and many other security mechanisms.
IKEv2 incorporates integrity checks, such as HMAC (Hash-based Message Authentication Code). It detects any tampering or modification of the transmitted data. These checks help ensure data integrity and protect against unauthorized changes.
It also supports Perfect Forward Secrecy (PFS). Even if someone gets the encryption keys, they cannot decrypt past or future sessions. PFS provides security by ensuring each session uses unique encryption keys.
The security of the IKEv2 protocol depends on the VPN provider, too. The protocol has no security vulnerabilities on its own; however, if the provider messes up with its setup, it could lead to issues. So, make sure you choose a VPN company that configures the IKEv2 protocol properly, like ExtremeVPN does.
How to Set Up IKEv2 on My Device?
Setting up IKEv2 on your device is easy; find a VPN service that supports the protocol, such as ExtremeVPN. Then, follow these steps for the installation process for macOS, iOS, and Android users:
- Get ExtremeVPN’s subscription plan.
- Install the ExtremeVPN app on your device.
- To switch to IKEv2, go to Settings, select the VPN settings option, and then choose the Protocol.
How to Set Up IKEv2 on Windows 11?
Here’s how you can configure IKEv2 on your Windows:
1. Click on the search bar present on the bottom of your screen (taskbar). You can find it right next to the Windows icon.
2. Type in “VPN” and hit Enter. It will take you to “VPN Settings.”
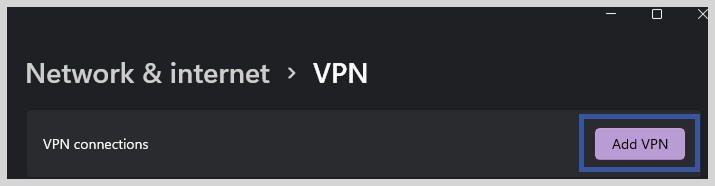
3. On the page, you will see an option “Add a VPN connection.” Click on it.
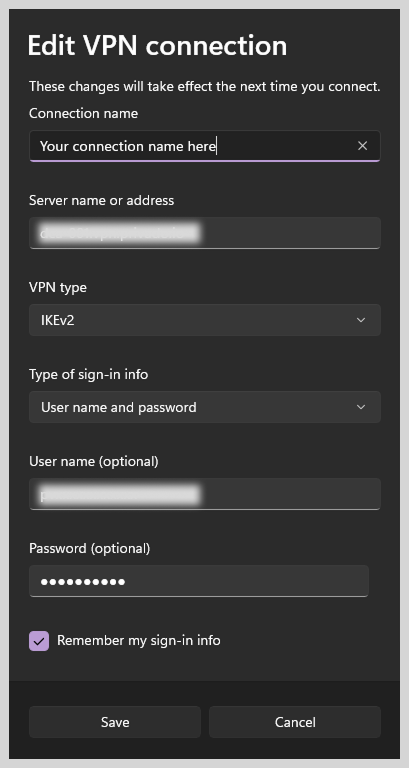
4. A pop-up window will appear. Here, you need to fill in the required data:
- VPN provider: Press on the side arrow and select Windows (built-in).
- Connection name: Write down any name you want to give (i.e, ExtremeVPN US Server).
- Server name or address: You need to add a server address here. (For example, 192.3.53.238)
- VPN type: Select “IKEv2”.
- Type of sign-in info: Choose the option based on your VPN provider’s requirements.
- Enter your sign-in credentials (username and password).
- “Remember my sign-in info” can be checked if you want to log in automatically without entering your password every time.
5. Save the settings.
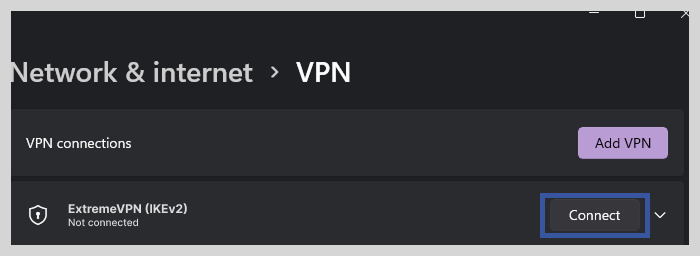
6. Click on Connect, and the VPN connection will be established with the required protocol, IKEv2.
How to Set Up IKEv2 on MacOS?
Follow these simple steps, and you can configure an IKEv2 connection on your Mac VPN:

1. Click on the Apple logo on the top right of your screen. It will display a window, select “System settings” from it.
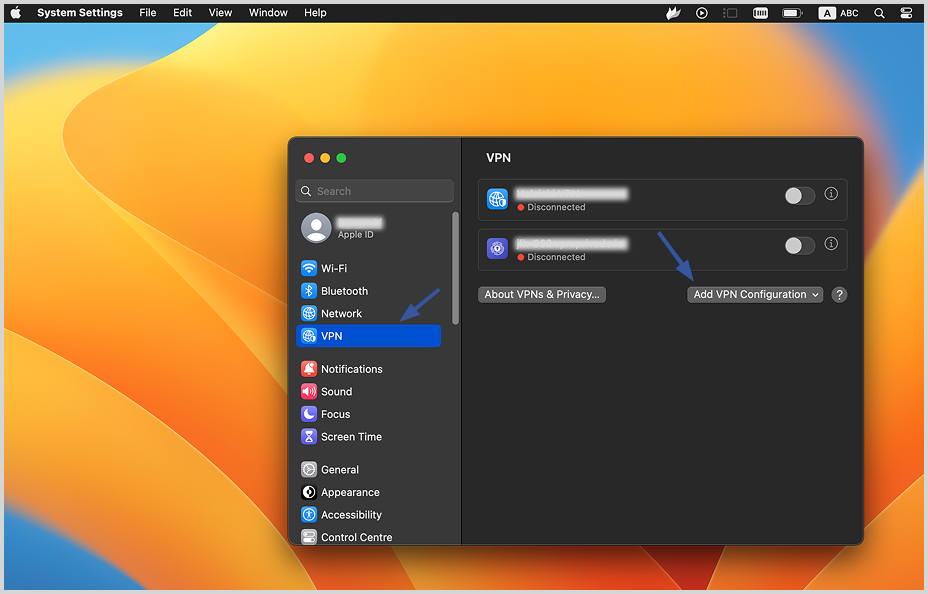
2. From there, select the VPN tab and then click on “Add VPN configuration.”
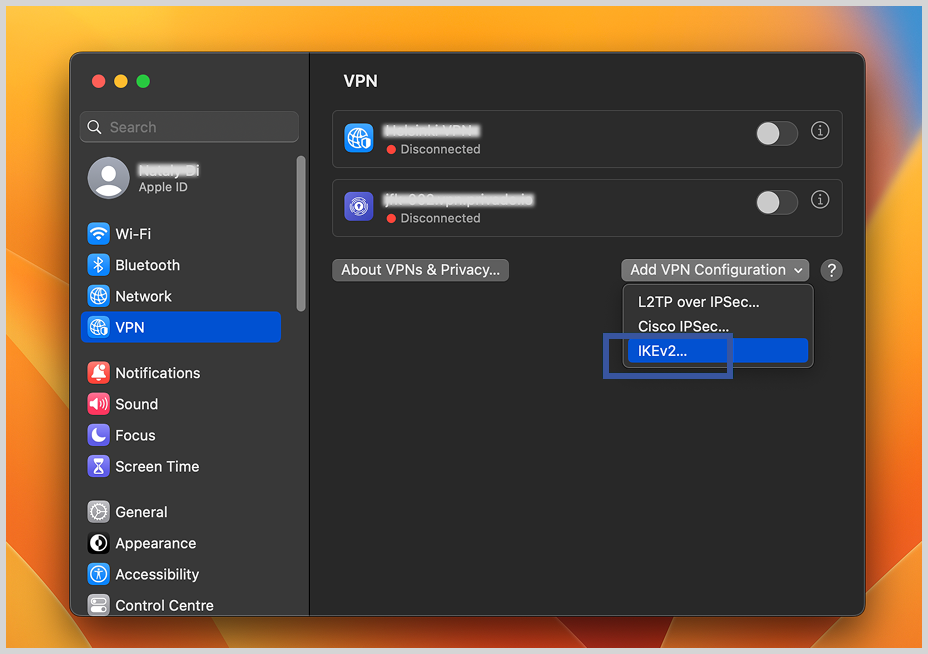
3. It will display a drop-down menu, select “IKEv2.”
4. In the next window, you need to configure the IKEv2 VPN connection settings:
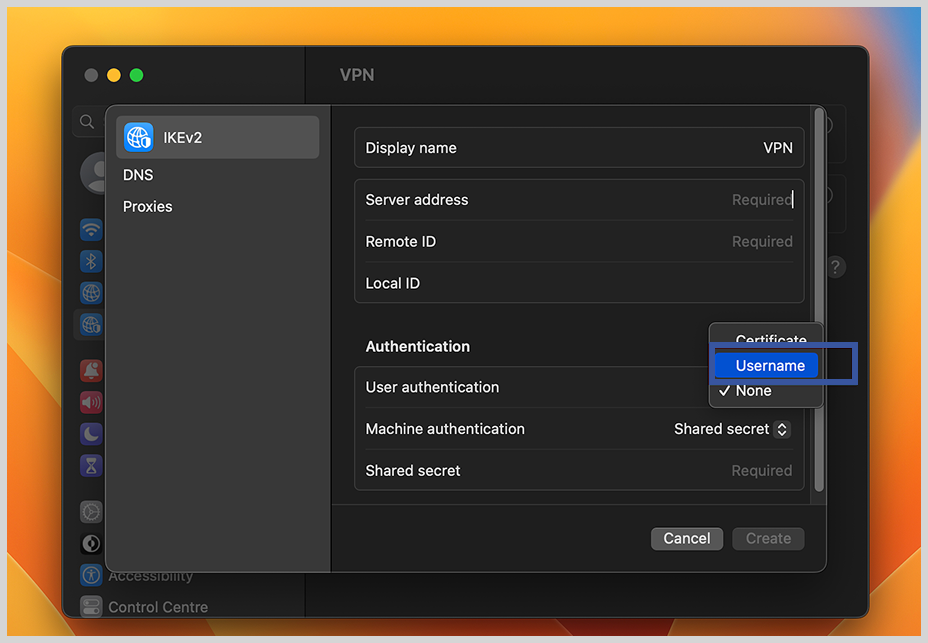
- Display name: It can be anything (i.e, EVPN or ExtremeVPN)
- Server Address: Enter the IP address or hostname of the VPN server you want to connect to.
- Enter the Remote ID and Local ID assigned by your VPN provider.
- User Authentication: Choose your VPN service’s authentication method. Select “Username” from here, and the IKEv2 VPN connection is almost ready to set up.
- Username: Enter your VPN account username.
- Password: Enter your VPN account password.
5. After configuring, click the “OK” button to save the changes.
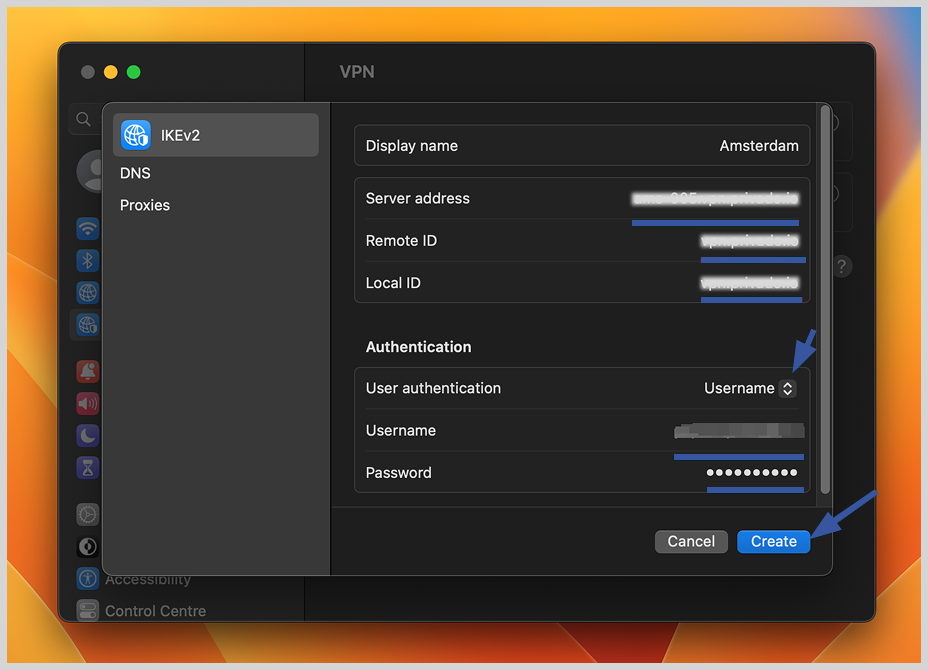
6. You will see the new IKEv2 VPN connection in the main Network settings.
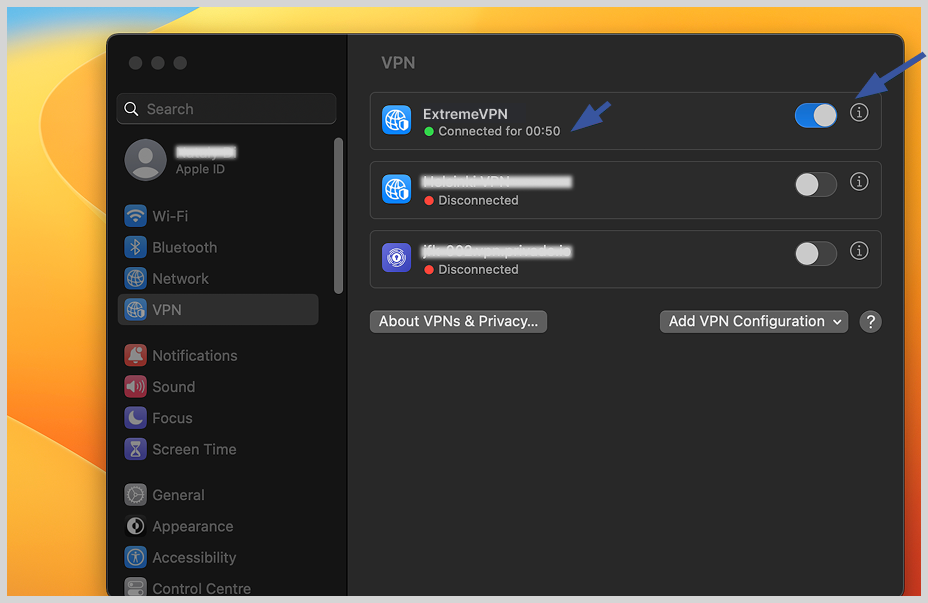
7. Click on the “Connect” button next to the VPN connection. It will activate the connection immediately.
How to Set Up IKEv2 on Android?
It’s easy to configure the IKEv2 protocol on your Android device. Here’s how you can do it:
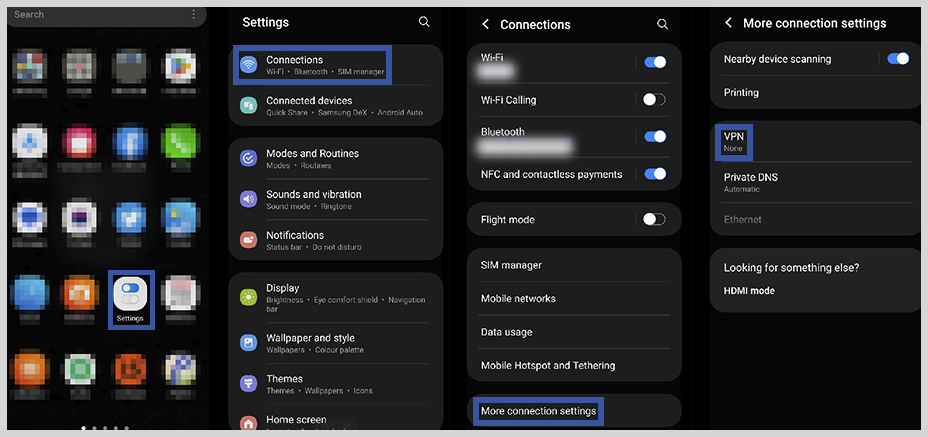
1. Open the Settings app. From the Settings menu, scroll down and tap “Network & Internet” or “Connections.”
2. Tap on “VPN.” It will take you to the VPN settings page.
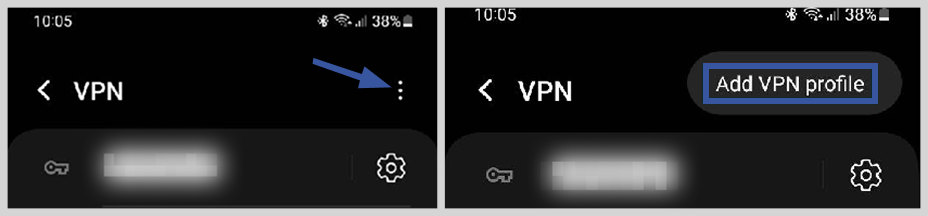
3. Press the three vertical dots on the top right of your screen. Click “Add VPN profile.”
4. In the next step, you need to do the following:
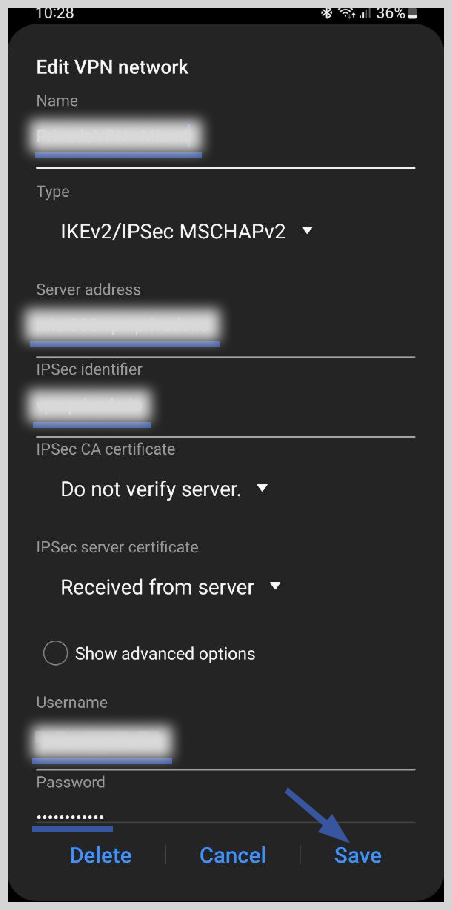
- Name: Enter a name for the VPN connection. You can name it anything you like.
- Server address: Enter the IP address or hostname of the VPN server you want to connect to.
- IPsec identifier: Add the code provided by your VPN.
- VPN type: Select “IKEv2/IPsec MSCHAPv2” from the list.
- Username: Enter your VPN account username.
- Password: Enter your VPN account password.
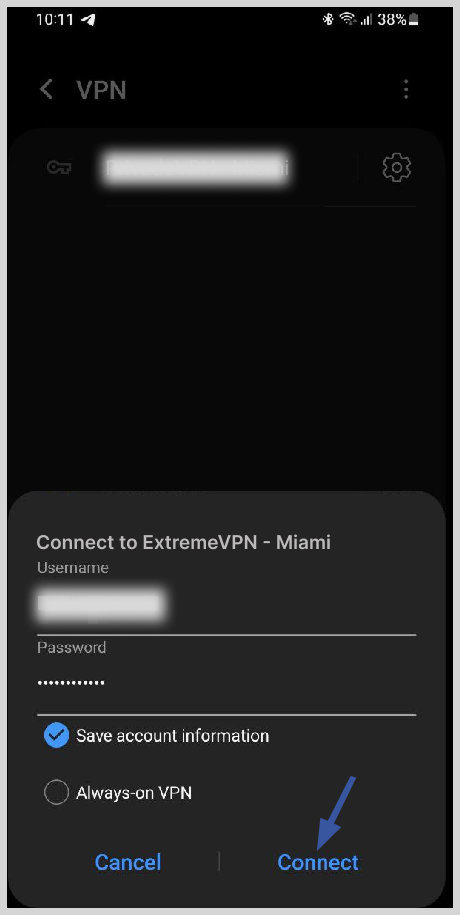
5. After entering the information, tap “Save.”
6. You will see the new IKEv2 VPN connection in the VPN settings.
7. To connect to the VPN, tap the “Connect” button. Once connected, a key icon in the status bar indicates the active VPN connection.
How to Set Up IKEv2 on Ubuntu?
Here’s how you can do so:
1. Open the terminal on your Ubuntu system. To do this, search for “Terminal” in the applications menu.
2. Type the following command in the terminal “sudo apt-get install -y strongswan network-manager-strongswan libcharon-extra-plugins;”
3. Then, go to “Connection Settings.” From there, find and choose “Wired Connections,” then click on “Wired Settings.”
4. Tap on the “plus (+)” sign next to the “VPN” tab.
5. Select “IKEv2.”
6. Enter the required information, i.e, username, password, and other important details about the VPN.
7. Press “Add” and save the settings.
8. Your IKEv2 VPN connection is set up. You can connect to the VPN now.
How to Set Up IKEv2 on iOS?
Follow the steps to configure the IKEv2 protocol on your iOS VPN:
1. Open the Settings on your device. Find and go to “General,” and tap on “VPN” to access the VPN settings.
2. Click on “Add VPN Configuration” to create a new VPN connection.
3. Here, provide the following details:
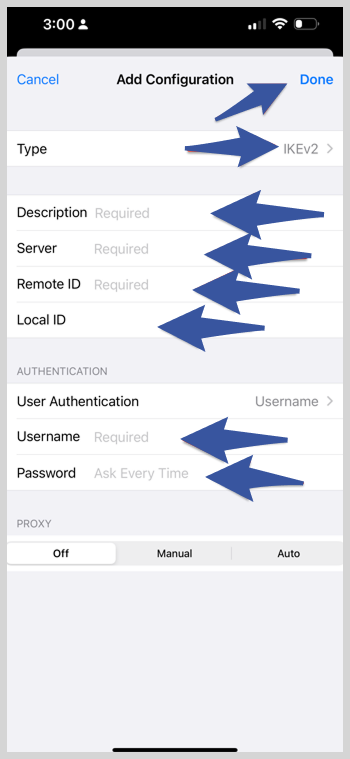
- Type: Select “IKEv2” as the VPN type.
- Description: Enter a name for the VPN connection. (i.e. ExtremeVPN UK server)
- Server: In the Server field, enter the IP address or hostname of the VPN server you want to connect to. (For example, 5.254.112.116)
- Remote ID: It’s the same as the server name.
- Local ID: Leave it empty.
- Enter your VPN account username and password.
- Proxy: Keep it off.
4. Tap on “Done” to save the VPN configuration.
5. You will see the new IKEv2 VPN connection in the VPN settings.
6. To connect to the VPN, toggle the switch next to the VPN connection to the “ON” position.
7. Your iOS device will establish the IKEv2 VPN connection within a few seconds.
What are the Benefits and Downsides of IKEv2?
| Benefits | Downsides |
|---|---|
| IKEv2 provides strong security for VPN connections. It supports robust encryption algorithms like AES and offers secure fundamental exchange mechanisms. | IKEv2 is not supported on other operating systems or devices like other VPN protocols. |
| IKEv2 is a stabile VPN protocol. It re-establishes connections after network interruptions or changes in network conditions. It handles switching between network interfaces effectively. | Setting up IKEv2 needs a more advanced configuration than other VPN protocols. |
| IKEv2 is well-suited for mobile devices. It is natively supported on most major mobile platforms, including iOS and Android. | In specific networks, IKEv2 traffic is restricted or blocked by firewalls or network policies. It limits its usability in those situations. |
| IKEv2 includes built-in Network Address Translation (NAT) traversal mechanisms. It allows it to bypass NAT devices and firewalls without requiring extra configuration. | By default, IKEv2 uses UDP ports for communication. While UDP is generally faster, some networks or firewalls might have stricter policies that block or restrict UDP traffic. |
How Does IKEv2 Compare to Other Protocols?
IKEv2 vs. SSTP
- Security: Both protocols offer high-security levels (AES-256 bit encryption). IKEv2 utilizes robust encryption algorithms, while SSTP uses SSL/TLS for encryption.
- Cross-Platform Support: IKEv2 has good cross-platform support. SSTP has limited cross-platform support for Windows platforms.
- Performance: IKEv2 is generally faster due to its efficient reconnection capabilities. In comparison, SSTP offers moderate performance.
- Stability: IKEv2 is highly stable once connected, while SSTP is more stable just on Windows.
- Firewall Compatibility: IKEv2 has good firewall compatibility. SSTP bypasses firewalls using port 443, commonly allowed for HTTPS traffic.
- Ease of Setup: IKEv2 setup requires moderate configuration. SSTP is relatively easy to set up.
IKEv2 vs. L2TP
- Security: IKEv2 provides high protection with strong encryption. L2TP relies on the encryption provided by the accompanying IPSec protocol.
- Cross-Platform Support: Both protocols have good cross-platform support.
- Performance: IKEv2 generally offers faster performance due to its efficiency in re-establishing connections. L2TP’s performance can be slower due to double encapsulation.
- Stability: Both offer a stable connection.
- Firewall Compatibility: Both protocols have good firewall compatibility.
- Ease of Setup: IKEv2 setup needs more configuration, whereas L2TP is generally easy to set up.
IKEv2 vs. OpenVPN
- Security: Both protocols provide high protection with strong encryption.
- Cross-Platform Support: OpenVPN has excellent cross-platform support. IKEv2 has good support but is not available on all platforms.
- Performance: IKEv2 offers fast performance, especially in re-establishing connections. OpenVPN performance can vary depending on configuration and network conditions.
- Stability: IKEv2 and OpenVPN are both known for their stable and reliable connections.
- Firewall Compatibility: Both protocols have excellent firewall compatibility.
- Ease of Setup: IKEv2 setup needs moderate configuration. OpenVPN setup can be more involved but provides more customization options.
IKEv2 vs. PPTP
- Security: IKEv2 offers high protection with strong encryption. PPTP has known security vulnerabilities and is less secure.
- Cross-Platform Support: Both protocols have good cross-platform support.
- Performance: IKEv2 offers faster performance. PPTP has speedy implementation due to its simplicity.
- Stability: Being an old protocol, PP2P disconnects frequently.
- Firewall Compatibility: Both protocols have good firewall compatibility.
- Ease of Setup: Both protocols are easy, but IKEv2 needs more configuration.