
The Dark Web is the part of the internet that one accesses using a particular tool. It is different from the normal web directories and stretches beyond any rules and regulations or censorship.
The dark web contains inaccessible onion links that you cannot access using Chrome, Firefox, Edge, and Safari browsers. For it, you need a Tor browser (onion router), which lets you visit the websites by rerouting your traffic through several nodes for anonymity.
Explore the hidden realm of the internet with our list of the best dark websites. Dive into the secret worlds of the dark web, learn what is it and what’s the difference between the dark web and the deep web. Also, explore the reasons why people access these onion sites. Some sites like Fark.com or Reddit.com help people to interact and share content, while others are purely for entertainment.
Best Dark Web Search Engines – Quick List

Here’s a rundown of the best dark web sites you can access in 2025:
- DuckDuckGo: It’s a privacy focused search engine, which is equivalent of a superhero and always there to save the day and keep you off the radar.
- The Hidden Wiki: There are hidden doors leading to the Dark web on The Hidden Wiki, the rebellious cousin of Wikipedia.
- Daniel: The enigmatic website with many fascinating text files and documents, much like a treasure chest.
- ProPublica: The investigative journalistic ninjas defending transparency, the truth, and holding influential people responsible.
- Sci-Hub: The scientific equivalent of Robin Hood, lowering the obstacles to scientific publication access even at the risk of upsetting some copyright holders.
- Hidden Answers: This dark web encyclopedia is prepared to respond to your urgent inquiries on subjects ranging from the intriguing to the blatantly secretive topics.
- SearX: SearX is an undercover search agent that collects information secretly from various sources without jeopardizing your privacy.
- Facebook Onion Site: Your privacy is a guest at this secret Facebook place on the Tor network.
- SecureDrop: Whistleblowers can use SecureDrop, the superhero hotline, as a shield to speak truth to power.
- BBC Tor Mirror: An intriguing addition to your news, the alternate reality BBC is available via the shadowy Tor network.
- Tor Metrics: The unsung hero who uses data and statistics to reveal the inner workings of the Tor network’s performance.
- ProtonMail: The encrypted email fortress where your correspondence is completely private and secure because it wears an invisible cloak.
- RiseUp: The tech wizards from below provide a safe means of communication for activists and organizers to carry out their noble work.
- SecMail: SecMail, the identity protection agency for digital superheroes, keeps your emails anonymous.
- Archive.today: Archive.today offers web portals for future generations, making it a paradise for web travelers and explorers.
- Mailpile: This email client is the modern-day Sherlock Holmes, figuring out privacy mysteries using encryption features.
- BlockChain.info: The detective of cryptocurrencies, searching the blockchain for information about digital transactions.
- ZeroBin: A digital graffiti wall with encryption that allows you to express your ideas anonymously and thrillingly.
- Wasabi Wallet: A Bitcoin wallet that keeps your transactions anonymous by dancing in the shadows.
- Imperial Library: The hidden library of the internet, where books and documents silently accumulate on the Tor network.
- Comic Book Library: It is a site on the dark web where you can find digital villains and heroes in an underground comic book store.
- Tunnels: A portal to the underworld featuring hidden passageways and unknown subterranean worlds.
- Deep Web Radio: Rebel radio station – playing songs only a black web lover knows how to dance to.
- Keybase: The encrypted knights protect the castle of safe messaging, file transfer, and group work.
- The CIA: Known for their intelligence work, they also have a knack for humor, showing that even serious organizations can have a funny side.
- OnionLinks: The entrance to the Dark Web, where various onion-themed websites are concealed.
- Ahmia: TOR Network guide and a lamp for the trail of the shining sun of the dark web.
- Dark.fail: A vigilante keeping watch over the world wide web, monitoring different services to ensure we will not be behind the trend.
- OnionName: The mysterious domain registrar for .onion domains on the Tor network.
- Elude: A search engine fire breather that helps you disappear into .onion pages in the dark web.
- Darknetlive: News and information portal that tells interesting stories from the edge of the digital world, where secrets live and tales are born.
How to Use a VPN with Tor – Quick Guide

- Select a reputable VPN service provider. ExtremeVPN’s lightning-fast speeds, impenetrable security, and expansive server network makes it the best among others.
- Install the VPN software on your router or device after downloading it.
- Launch the app, then select a server of your choice.
- Start anonymously and safely perusing onion websites.
Caution: Prioritize Safety When Visiting Dark Web Sites

When exploring the dark web, there are important measures you should take to ensure optimal security. For example, you must use anonymous web browsing software such as Tor, a VPN, and an antivirus. The onion browser Tor provides an extra layer of security using its nodes. The VPN encrypts your internet connection, keeping your identity hidden. And the antivirus is capable of blocking virus attacks. You also have to be careful not to share your private information.
One should also remember that higher authorities can supervise the activities taking place on the dark web. For this reason, visiting some of the sites on the dark web may result in being held criminally responsible for the acts carried out within them.
Top Dark Web Websites 2025 – Detailed List
Although the dark web does not have friendly search engines, people can still surf around the internet and explore its content. However, remember to use the Tor browser and a VPN when visiting these hidden sites.
1. DuckDuckGo
DuckDuckGo is a stand-alone business that sells items designed to protect online privacy. The search engine is the company’s flagship product and its official name, Duck Duck Go Inc. Since then, it has released extensions for external web browsers that prioritize internet privacy and its web browser. The classic kid’s game Duck, Duck, Goose inspired the name DuckDuckGo.

The DuckDuckGo website is made with user privacy in mind, making it one of the best onion search engines. The business doesn’t store identifying information, track users, or save user IP addresses. It also doesn’t keep track of the websites or search histories that its users have visited.
DuckDuckGo doesn’t connect any terms with users; it only keeps track of aggregate search terms. The onion site does not have any search or browsing history that it could give to governments or law enforcement agencies because of these practices.
2. The Hidden Wiki
The Hidden Wiki is the unrestricted link directory listing all the significant .onion links. Like regular Wikipedia, users can make changes anonymously after registering on it. It’s a fantastic place to start when researching the content on the dark web. However, exercise caution—many fake, illegitimate, and dead links are present in its directory.
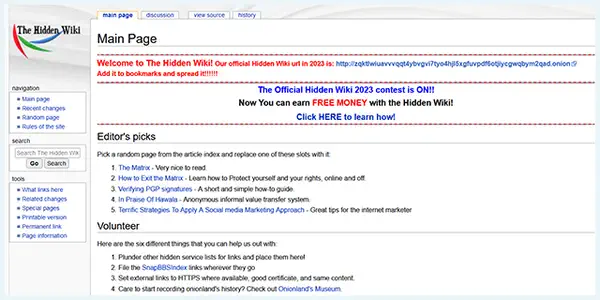
In addition to marketplaces, forums, and other websites not indexed by search engines like Google, it acts as an index for various hidden services. The Tor Browser is the only way to access the Hidden Wiki. It lets users access the web anonymously by passing through several encrypted layers.
3. Daniel
There are almost 7,000 .onion addresses on Daniel, the Onion website. They are further classified into different categories so that it will be easier for one to browse through.
Furthermore, the website comes with an in-built testing feature that checks the functionality and active status of onion sites. Learning about Tor starts by visiting Daniel’s website, which helps determine whether a Tor site is functional and when it was active last.
Unfortunately, Daniel took down its onion link list in August 2023 since it was not possible for one person to monitor the entire dark network. The site also contains some fun and educational blog posts and technical guides.
4. ProPublica
ProPublica does investigative journalism. In 2016, the site won the Pulitzer Prize for analyzing a story on sexual abuse cases. To reach Propublica, one uses a normal internet interface called cleanNet. The latter ensures its site is available on the Tor network for those willing to use it. You may access it via a Tor browser to bypass country bans and enhance security and anonymity.
ProPublica is among the best-designed websites you can find on the dark web. Additionally, you can use Tor to read news websites like The New York Times and others and utilize their SecureDrop integration to report news of interest.
5. Sci-Hub
Although several paywalls restrict numerous scholarly articles, Sci-hub aims to provide all research projects for free. There are currently over 88 million studies in the site’s database, and about 80% of it consists of journal research articles.
Remember that Sci-hub is prohibited by copyright in some nations, so before using or downloading any of Sci-hub’s papers, you should confirm the legal requirements in your area.

Although the Onion link is no longer active, you can access it on Tor using the standard link. Additionally, you can try Sci-hub’s mirrors (sci-hub.ru and sci-hub.st) if you discover that the site is unavailable.
6. Hidden Answers
Hidden Answers is one of the most popular sites on the deep web. The site is just like Yahoo Answers, Quora, and Reddit, but on the dark web. If you have any inquiries regarding the dark web or are unfamiliar with this area of the internet, this is a great place to start.
For particular inquiries on the dark web, it’s safer to check out some of the subreddits.
Once you log onto the website, you’ll quickly observe that the questions cover many subjects. Even with the internet’s greatest anonymity, people still want to know the origin of your nickname and whether you want your head cryo-frozen when you pass away.
7. SearX
You can use SearX as a metasearch engine on both the dark web and the surface. To preserve your privacy, it doesn’t share IP addresses or search histories.
Furthermore, it disables tracking cookies to avoid results based on user profiling.

We will submit your queries via HTTPS POST to prevent keywords from appearing in the website’s server logs. Another best feature of this website is the ability to search for in-depth questions. You can search for documents, photos, videos, maps, social network posts, and more.
8. Facebook Onion Site
There are many unexpected websites on the dark web, and the Facebook Onion site is one of them. While we advise against using Facebook if you wish to maintain your anonymity, it’s interesting to see how prevalent this social media platform is ever since it joined the dark web in 2014.
This website is a replica of actual Facebook. You can create a Facebook profile on the dark web by using an alternate username and email address, just like you do on the original platform.
However, identity verification may be impossible since Facebook is known for collecting personal data. Some people use it as a workaround for government censorship in certain nations. With Facebook’s dark web version, users can try to remain anonymous while speaking freely.
9. SecureDrop
The dark web is one of the few places whistleblowers can share information, knowing they won’t be followed. The website, SecureDrop connects Journalists and whistleblowers.
Several significant newspapers and publishers have created unique SecureDrop URLs after realizing the potential of anonymous leakers on the dark web.
Additionally, SecureDrop significantly reduces the possibility of an initial metadata trail from communications with journalistic sources. Furthermore, it aims to offer a more secure medium for those exchanges than the potentially vulnerable regular corporate news networks.
10. BBC Tor Mirror
Some governments and nations enforce strict internet censorship to prevent people from reading foreign news sources. The BBC website is one of the best examples of a news source that is unavailable in some repressive nations.
The news website of the BBC has been mirrored on the dark web by a dedicated Tor mirror. The intention is to provide an unrestricted, anonymous means for anyone, anywhere in the world, to visit the BBC website.
11. Tor Metrics
The dark web is filled with interesting topics because it appears popular with shadowy characters and is difficult to use. What would happen, though, if we quantified all that activity? The website that tracks who and where the network users are is called Tor Metrics. It may surprise you that 20% of all internet users are Russian. Second place goes to the US, with about 18% of the market.
The data indicates that not many people use Tor daily—approximately 1.5 million—and shows the size of the network. This figure shows that there are a little over 60,000 distinct .onion addresses.
12. ProtonMail
Proton Mail, a Swiss encrypted service, is one of the best onion sites and email clients. They don’t keep any logs and employ end-to-end encryption. Furthermore, the website doesn’t asks for your personal information when creating an account on it.

According to Proton, there are security benefits when utilizing Tor to access Proton Mail’s dark web version. It is more difficult for outside parties to view the sites and mail services you visit using the Tor browser. Furthermore, Tor can work around a country’s blocking of ProtonMail.
13. RiseUp
Riseup offers chat and email services without storing any information about your usage. Unlike Google, it is safe from hacking attempts and has no plans to work with any government. The site supports causes like “Human freedom, proper care of animals, and environmental sustainability.” In addition, Riseup offers mailing lists, organizing tools, and more.
You need an invitation code to create a Riseup account; knowing the dark web site address is insufficient. You may still persue the security section, though! It offers great advice on incorporating information security into your day-to-day activities.
14. SecMail
Among the most widely used email services available on the dark web is SecMail. However, the site’s drawback is that each user’s data can only flow at 25 Mbps. It is sufficient for PGP-encrypted messages, even though it is not much compared to traditional email services.
Unlike several similar services, secMail email security is more than just a mail filtering service. SecMail stops spam from being received by identifying and blocking it while it’s still in transmission. Typical email servers then send the messages back to the sender along with a delivery block message that includes the error description from SecMail.
15. Archive.today
This website is a web page time capsule. Even if the initial posting disappears, it can preserve a version of the webpage that remains accessible online. It is a useful tool for getting a quick screenshot of a page on the internet that may change soon, like job listings, pricing pages, or real estate listings.
You can access a selection of available snapshots by entering the URL of the website you want to view snapshots from. Even archived websites are available for download as ZIP files.
16. Mailpile
Mailpile helps to recover private online communication, giving users control and ownership of their email data. It is a project to save our personal lives from the exclusive cloud and stop government and corporations from spying on us through the strip-mining of our conversations. Regardless of how many messages you have—thousands, millions, or even just a few—you can manage your inbox with the help of robust search and tagging.

Thanks to its quick and responsive design, Mailpile outperforms “the cloud” even on sluggish computers. It also functions when the web is unavailable. Encryption and OpenPGP signatures are not an afterthought but an integral part of Mailpile’s design. Ironically, most web-mail services remove spam only to insert their adverts in its place. However, Mailpile is ad-free.
17. BlockChain.info
Users can explore the murky depths of the dark web by using the Tor network. Because of Blockchain.info’s extra security and anonymity features, it will be very difficult to link the Bitcoin transactions to the actual people.
The Tor network gives users access to the dark web, or hidden corners of the internet, for those who value privacy and anonymity. Because Blockchain.info transactions provide additional security and anonymity, it can be difficult to track the movement of cryptocurrency and connect it to the real parties involved.
18. ZeroBin
Similar to Clearnet, Tor has useful web portals, and ZeroBin is among those. You will need a method to share content with other dark web peers if you are a frequent user of the Tor network. You can do that in total privacy and safety with ZeroBin.
One of its selling points is that even ZeroBin servers are unaware of what you copied. Your browser encrypts the data before sending it to the server. Password security is one of the sharing options. Naturally, the pastes will be removed at a later time.
19. Wasabi Wallet
A well-liked wallet for cryptocurrencies on the dark web, Wasabi Wallet is a secure option for receiving and sending funds. Since the code is open-source and completely free, almost anyone can edit and verify it.

Using the website’s “coinjoin” function, multiple cryptocurrencies can be combined into a single transaction. It makes it challenging for third parties to locate your money. Additionally, Wasabi Wallet is non-custodial, meaning only you can access your personal encryption keys.
20. Imperial Library
Like the Comic Book Library, the Imperial Library has a huge collection of digital books accessible via the dark web. It extends to the Imperial Library, where a wide range of materials are available in addition to comic books.
Approximately 1,500,000 books are available at this online library as of the time of this writing. Once more, watch out for copyright violations. If you accidentally violate someone else’s copyright, you may have to conceal your IP address.
21. Comic Book Library
Do you enjoy comic books? You can download hundreds of comic books from the Comic Book Library, ranging from highly popular titles to niche comics. Just be mindful of potential copyright violations when using the Comic Book Library (or another Onion site) to access comics.
If you unintentionally come across any copyrighted content, we advise using a quality VPN like ExtremeVPN. We know you mean well, but if you inadvertently read content protected by copyright without using a virtual private network (VPN), your IP address may be registered, putting you in danger of legal repercussions.
22. Tunnels
Tunnel exploration at US universities is the subject of some of the most well-known Tor websites. Such infrastructure is illegal to access and dangerous to use. For this reason, blogs run by urban explorers are hosted on Tor.
The smaller blog, IIT Underground, focuses on Illinois Tech. Virginia Tech is more noticeable beneath VT. It offers more information about the tunnels and the risks connected to them. Additionally, the website’s designs surpass those of the typical Tor website. However, they continue to resemble things from earlier times.
23. Deep Web Radio
Do you want background music to accompany your exploration of the dark web references in this writing? Fortunately for you, the dark web features a digital radio station.
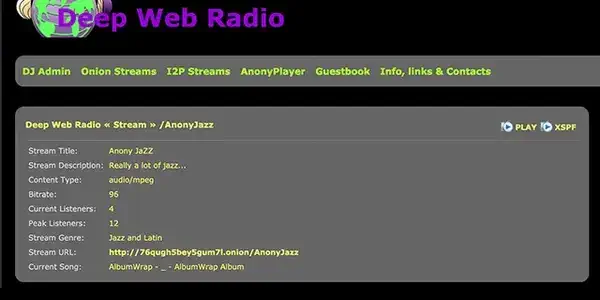
You can select from various music streams over Tor with Deep Web Radio. When we looked, there were eleven channels to choose from, each playing a different genre of music.
24. Keybase
Keybase securely allows you to share data you discover on the website Tor with your peers and other contacts. It’s a useful messaging tool that functions similarly to well-known messaging apps like Signal and WhatsApp. The platform’s greatest feature is that its servers are unaware of the content you copy and paste.
After all, before it ever reaches Keybase’s server, your data is encrypted in your browser. Additionally, you can set a password to secure your message and determine when it will expire.
25. The CIA
For those who wish to interact with the CIA anonymously, the agency has opened a shop on Tor. Everything on the main website will be accessible, including job postings, CIA contact details, and historical data such as the World Factbook. The primary distinction is that you can contact the agency without worrying about being followed.
We advise getting additional protection if you can’t bear the thought of being identified or if the data you share is compromised. For even greater anonymity when exploring the dark web, consider using a high-quality VPN service like ExtremeVPN. Additionally, this will add another level of data encryption, enabling secure communication with organizations like the CIA.
26. OnionLinks
OnionLinks lists operational dark web pages. The website is clear and well-structured. Each link is categorized as financial services, business services, news websites, email providers, and security services.

Remember that not all of the dark web websites that OnionLinks provides are 100% secure. Whenever you visit any of these pages, we advise using a robust antivirus program like Norton 360 to protect you from malware.
27. Ahmia
Ahmia describes itself as a concealed service search tool, and that’s exactly what it does, even though it’s difficult to determine which engine performs better. Content about child abuse can also be eliminated from search results. It’s a useful service for individuals who wish to explore the dark web.
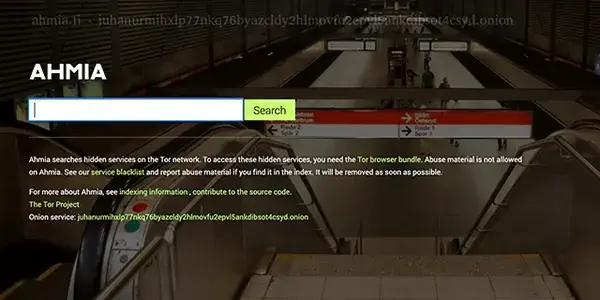
But keep in mind that using Tor is difficult. Most of the Tor network isn’t indexed, making it invisible to search engines and being cut off from the regular internet. The network is essentially made up of hidden web portals.
28. Dark.fail
With the help of the handy platform Dark.fail, you can keep an eye on the uptime of different .onion websites. Put differently, it lets you see which well-known dark sites are active at any given time. It also offers precise URLs that have been PGP-verified. There is no tracking or JavaScript manipulation on the website. Many websites listed here are among the fifty websites that Dark.fail currently monitors.
While not particularly impressive, the majority of well-known websites are included. You can also get in touch with the team to suggest new listings. Be aware that Dark.fail only keeps an eye on how many top dark websites are up and running. Since it doesn’t check for malware, it cannot inform you if these are safe. For this reason, we suggest to use a reliable virus scanner like Norton.
29. OnionName
Usually, domain names for darknet sites consist of a random combination of characters and symbols. OnionName is a great option if you’re looking for a domain name for your dark website that makes sense to people. It is an innovative platform that allows you to personalize your online presence by creating a unique domain name with any combination of words or letters you desire.
With a simple registration process and a specific amount of millibitcoin (mBTC), you can easily establish a distinct online identity that reflects your personality or brand. Say goodbye to the limitations of traditional domain names and hello to the freedom of choice with OnionName.
30. Elude
Elude, an email client, has a goal to keep your emails private. Through webmail, users can exchange anonymous emails. No information is needed to set up an Elude account. The service is a great and free option for sending private and sensitive information via mail.
Every server on the Elude network is hidden and is hosted on the Tor network. It indicates strict protection for all user data and no government eavesdropping. Also, the Tor protocol removes all traces associated with your identity.
31. Darknetlive
Users can find articles about the dark web on Darknetlive. Articles with fascinating facts, pictures, and official quotations are frequently released. A handy list of dark web vendors is also available on Darknetlive; it provides comprehensive details about each vendor, including .onion addresses and FAQs.

You can use the list to steer clear of dubious or unlawful marketplaces. In addition, Darknetlive provides a list of resources for cryptocurrency enthusiasts, a collection of dark web forums with descriptions that include screenshots, .onion addresses, and an extensive collection of dark web links with descriptions for each website.
What are Onion Sites?

Onion sites are websites that are only available on the dark web. These sites are browsable by Tor and other networks that avoid regular search engines like Google or Bing. You can’t normally surf onion sites with Chrome, Firefox, or Edge browsers. To access onion sites, you must download a special browser invented by the Tor project.
No ordinary domain names are registered within the domain name registry for onion/dark net websites. However, they are created using a cryptographic accessible via Tor only. Through volunteer-operated nodes, it passes internet traffic throughout the world. Over 6,000 relays in this private network ensure nobody will find out where you are from.
You can use the Tor browser to surf the regular HTTPS sites on the web. You will improve your privacy using the Tor browser, as it provides isolation whereby no third-party tracker or ISP can reveal your identity. On the other hand, tor is not always appropriate. Onion routing makes your internet very slow but provides anonymity. Therefore, we do not advise relying on Tor to carry out data-exhaustive tasks such as HD streaming, playing games, torrent downloads, and video calling.
What is a Dark Web, and How Does it Work?
The dark web comprises a facet of the internet that users cannot access on common search engines like Google, Yahoo, and Bing. It is a restricted network that uses a special technology and encryption called “Onion Routing.” To access it, you need a special setup, an onion router, which passes your internet traffic through several forms of relays.
Difference Between the Deep Web and the Dark Web
The internet comprises three main parts: the surface, deep, and dark web.
The Surface web is the narrowest space of the internet. Anyone and everybody can access it without any setup. It can be accessed using typical browsers or search engines. It includes sites such as Facebook, Wikipedia, online commerce sites, and YouTube, among others.
The deep web and the dark web are often misunderstood to be the same, but they aren’t. Unlike the surface web, the deep web is the part of the internet you cannot find with your everyday search engine. Access to this part of the web is protected via a password. Furthermore, logging in or from one’s specific IP address or URL is necessary to access such deep web information.
Some of the deep web sites also use unusual TLDs like .gov, .com, or .net, which normal browsing engines will fail to track down. In other situations, some sites will blatantly deter search engines from identifying their location.
Then, a part of the deep web is the dark web which is only accessible through special software and tools. You need to access the dark web using anonymous tools such as the Tor browser or I2P. Also, some people claim that the dark web requires an invitation by a person in order to access it.
The dark web is home to many illicit activities. For example, various illegal goods and services like drugs, guns, identity thefts, pirated software, malware, and other contraband can be found on the dark web marketplaces.
The Dark Web also contains a wide assortment of genuine information and activities that people use daily. For instance, it gives the users privacy by allowing access to information not found in the open space and sharing information in secrecy and anonymously.
Though the dark web has both pros and cons, it is important to note that the risks here far surpasses than the advantages. Therefore, it means that when going for it, you need to be careful.
Tor Browser and the Dark Web: History & Connection

The dark web originally began as a tool for communication amongst governments, big corporations, hackers, and black markets. However, technologies that involved encryptions and the Tor browser allowed the public to get through to them.
In the late 90s, The US Naval Research Laboratory developed The Onion Routing (Tor) project. Today, many sites under the .onion registry operator are accessible through a network browser.
There is no privacy on the internet since it cannot be restricted only to a certain population. The armies made the first generation of Tor to cover up spies’ communications. Eventually, this framework was revised and rolled out as an SSL browser.
Tor is similar to a normal browser like Firefox, Google, and Safari. It offers the same tunneling as on other browsers but provides extra security and passes your traffic through certain random nodes before reaching its final destination. It implies that you leave no traces of your online activities and no exposure to your browser’s browsing history.
Legitimate Reasons Why People Use the Dark Web
Read on to learn why people tend to explore the dark web:

- Activists who advocate for democracy utilize the dark web to communicate in highly secure areas like China and Iran. The anonymity of the dark web gives them a medium for accessing information that can’t be easily obtained.
- Dark web proves to be helpful for people living in restrictive environments. They might not find access to social media portals such as Facebook because of government restrictions and use it to visit such sites.
- Since the dark web offers more freedom, journalists use it to shield themselves and their sources’ privacy.
- Most users searching the dark web seek anonymity due to non-observance of others’ online activity, traffic, and geographical position, among other things.
- Some individuals may not like talking openly about their medical problems. Using the dark web is how they try to get some medical advice.
Ways to Access the Dark Websites
Mozilla Firefox
It is easy to enter the dark web using Mozilla Firefox. You only need to alter its settings. Follow these simple steps:
- Open the Mozilla Browser.
- In the search bar, type “about:config” and enter.
- Here you have to find “network.dns.blockDotOnion.”
- Change the settings to “False.”
- Restart the Mozilla browser and start surfing.
Before going into the depths of the deep web, ensure the NoScript and HTTPS Everywhere plugins are installed on your Firefox browser.
Subgraph OS
This system offers improved security as well as a high level of privacy. It is written in Tor browser code. The specifics comprise kernel hardening, application firewalling, package-level safety, filesystem encryption, meta-proxy encoding, and binary integrity.
In a nutshell, the Subgraph OS is a secure, privacy-orientated operating system that users can use in high-risk environments. You may also choose Subgraph OS as an additional alternative to Tor.
Invisible Internet Project
I2P, known as the Invisible Internet Project, is used to browse and navigate both the surface and the dark web. For example, one can access DarkWeb via I2P, which is made possible through the Tor plugin of Orchid Outproxy. A layered program runs the user’s data through it to deny access to the dark web and ensure undetectability.
Another essential security characteristic in this case is that everything entering the app from external sources, like private and public keys, is also encrypted. Its unique aspect lies in utilizing file storage that lacks any central agency through the Tahoe-LAFS plugin.
Whonix
It is also compatible with other platforms such as macOS, Linux, and Windows. Ensure your Whonix experience is similar to Tor’s, as they share the same underlying source code. There are, however, major differences within the background, despite the similarities.
Another instance is where an employee accesses Whonix’s virtual workstation machine through the internal virtual LAN. However, it can only communicate to the gateway, which is the best way for the browsers to protect user apps from getting the device’s IP.
According to the creators, despite being strong, their technique would make it impossible for any malware to detect the machine’s IP address regardless of whether it possesses root access. You should also note that Whonix is not a single browser. It is part of Whonix, an all-in-one OS that runs within a virtual machine (VM). This comprises the whole package of productivity programs such as Word software and a mail client.
The Legality of Accessing the Dark Web

Viewing and navigating the dark web is not illegal. Despite having the cons, the dark web is also used for legitimate purposes, and there are many advantages you can get from it. For example, it protects your privacy and lets you view unverifiable content and services.
Moreover, the ability to remain anonymous has made the dark web a haven for people whose existence would be compromised by using the surface web. Some of these people are whistleblowers, abuse, persecution, and activist victims, as well as politicians. Conversely, it also forms a conducive environment for crooks and other criminals who engage in illegitimate actions.
As a result, the validity of the dark web will be determined by what you do with it. Some people use it for fair purposes, while others on the dark web carry out illegal activities. Note that it is easy to find yourself in trouble when you act illegally and compromise other people’s security and liberty.
Is Using the Tor Network Legal?
No legal restrictions are associated with using anonymous browsers like Tor or I2p. They do not target the black market solely. In recent years, several individuals have utilized the Tor browser to browse the surface of the net and explore the hidden recesses within the dark web.
The anonymity of the Tor network becomes necessary due to growing online privacy concerns today. That is how one can avoid third parties monitoring their online activities. Countries that heavily censor their internet traffic will necessitate a Tor Browser or VPN for people to access the surface web.
It is important to note that even though Tor protects your privacy, you may still be charged if you engage in any criminal activity. For instance, no one should download pirated copyrighted material involved in terrorism or sharing of illegal porn. It does not mean such actions are right because you use an anonymized browser.
Dark Web Common Misconceptions
The dark web is a hidden network, which means anything you post or say on it always stays secret for open internet users. Therefore, it enables parties to bypass governmental barriers, hence facilitating unlawful conduct such as drug trafficking and weapon smuggling. However, the dark web is a bit mysterious and is often misunderstood.
Here are some common misconceptions that you should know about the dark web:
- You can access it with your regular browsers.
- Everything on the dark web is free to access.
- It is only used for illegal activities.
- All the content and sites on the deep and dark web are dangerous.
- No one can track your activities on the dark web.
- Dark web is illegal to use in every country.
- It is only used by criminals and hackers.
- Only the banned and prohibited goods are sold on the dark web marketplaces.
Types of Threats Associated with the Dark Web

Is it safe to operate on the dark web? Well, it can be risky. For this reason, you should not just see the dark web as a place for general privacy. Common dark web dangers include:
Scams
A vast portion of what passes for “service” on the dark web are elaborate lies and frauds. Other services are real; if you need something, you will receive it after reaching a certain price agreement. Unfortunately, some individuals utilize the dark web’s image to scam people. Malicious hackers may use phishing to steal your data, extort you, or access other sensitive materials such as intellectual property.
Government Monitoring
Various government bodies monitor the best Tor sites around the world. Some even express concerns, for example, if this implies that law enforcement can monitor the happenings on the dark web, so to speak, as in the case of Silkroad site administrator, one of the biggest illegal marketplaces in the so-called deep space. Law enforcers can use custom software to penetrate the dark web and detect activity analysis.
Even if there is nothing wrong with what you do, you can still be watched over — very closely. Some countries regard evasion of government dictates for new political beliefs as a punishable crime. One of these is, for instance, the Great Firewall, whereby China blocks any Western website it considers harmful. Accessed information may also make you end up on a watch list or be targeted for imprisonment.
Malicious Software
The dark web can help criminals to infuse malware into your devices. Therefore, any unaware individual can get infected through the devices they use. Unlike most sites on the surface web, many .onions don’t take essential steps to give user protection.
They can expose you to botnets, ransomware, keyloggers, and phishing viruses. Therefore, by visiting dark net sites unprotected, you expose yourself to potential attacks that may target you. This danger may spread to your collection of smart devices networked on the internet.
Tor protects you when browsing the dark web, but other things about your online activity will be a trail that will give away your real identity. Therefore, you should only rely on a trusted VPN like ExtremeVPN for greater safety and anonymity.
Tips to Stay Safe When Accessing the Dark Web
If you’re trying to enter the dark web, make sure you do so safely. These tips will help you:
Separate Your Real Life from Your Online Persona
Never expose your data on the dark web. Wherever possible, develop fresh burner accounts and documents. Use prepaid and anonymous credit cards for secure transactions while buying from the dark web. Make sure to refrain from using payment methods that disclose your identity.
Trust Your Instinct
You should always be on alert while on the web and trust your gut feeling. Do not take it at face value. Most people are not what they appear to be. Also, beware of the dark web links you visit and the media you consume. Only open any site if you feel it might be correct.
Use Active Monitoring of Financial and Identity Theft
Several online facilities now provide identity security. Hence, it is compulsory to ensure that you secure the services of a trusted supplier for safety when using the dark web.
Disable Java and ActiveX in Your Network Settings
Hackers can use ActiveX or Java vulnerabilities to compromise the systems with these frameworks. Therefore, you shall turn these off in your network settings at places where you will encounter various threats that make you unsafe.
Avoid Downloading Dark Web Files
There are many types of malware infections in the dark web because it has no control. Therefore, you should only open dark web attachments if necessary and avoid downloading all the files that appear here. In addition, ensure that you run a thorough dark web scan using advanced antivirus software when downloading files.
Use a Secondary Non-admin Account
Your main account comes with admin permissions, which can pave the path for malware attacks. By using a non-admin account for everyday tasks, you can protect your system from malware that tries to penetrate admin permissions.
How to Access Onion Sites Safely

The Tor browser enables anonymous internet browsing and access to unavailable websites. It encrypts your traffic and data, leaving no way of interception for anyone.
Nevertheless, other entities like the government or your ISP will be able to tell that you are communicating via a Tor. Moreover, the browser has mostly become synonymous with illegality. Such practice raises red flags as it might be illegal according to the legislations of certain states where the ISPs fully limit Tor connection.
One useful tool for disguising Tor activity is a virtual private network (VPN). A VPN routes your traffic through a different server and adds an encryption layer, protecting your Tor usage from prying eyes.
ExtremeVPN – The Best VPN for Dark Web Websites
ExtremeVPN is the best VPN choice for accessing tor sites. It supports the safest and most trusted VPN protocols, including IPSec/IKEv2, WireGuard, and OpenVPN. These protocols assure you of the best P2P sharing, encryption, streaming, and speed.
Moreover, we have dedicated apps for all popular devices, including Windows, Mac, iOS, Android, and router types. Its easy to install and requires no special configuration.

Our VPN has over 6,500 servers in 78 countries. Each of those countries is home to users of the best server to get into it. Additionally, it supports a maximum of ten devices at any given time. Users do not have to log out from one device to connect with ExtremeVPN on another.
Additionally, ExtremeVPN provides unlimited bandwidth, thus allowing users to enjoy anything without worrying about data limits. It offers users with high data transmission rates that enables them to stream, game, scroll, download, upload, and do anything without buffering or slow load times.
Also read: Tor vs. VPN: What Are the Differences?