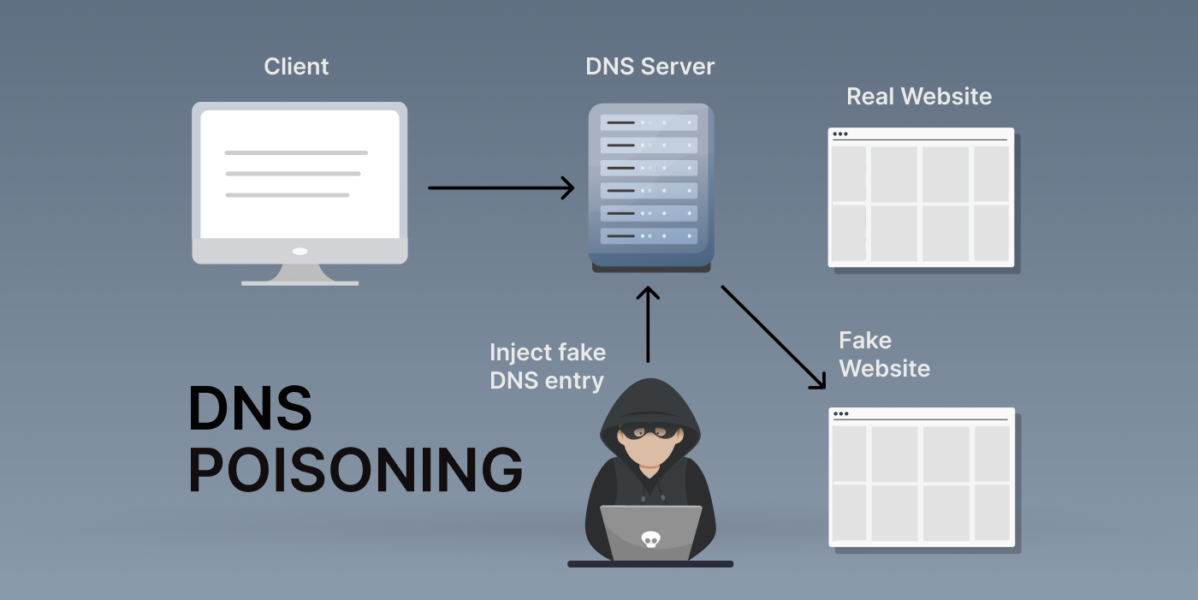
Cybercriminals are constantly roaming the internet, searching for their next victim to attack using various tricks. One such tactic is DNS cache poisoning. This process not only diverts internet users from their original search query but also leaves them vulnerable to many risks, such as malware and data theft.
In this article, we will explain everything you need to know about cache poisoning, including how it works and how you can prevent it from happening.
What is DNS Cache Poisoning?
DNS cache poisoning is a cyber attack in which hackers insert false data into a DNS server. That way, the DNS query will return a wrong response, and users will be redirected to an incorrect web page. In simpler terms, it’s a process where criminals corrupt the DNS cache of a device or server.
For every online search you perform, your device and DNS server store cache information, becoming the main DNS poisoning target.
If your cache gets poisoned, you will be forced to enter a hacker’s site, regardless of if you entered a legitimate and correct URL. This malicious site can infect your device with malware and viruses and even put you at risk of data theft.
What is the Domain Name System (DNS)?

Just like how you have a phonebook containing your contact list, a DNS serves as a directory that hosts every site you want to visit. The DNS allows a site URL to get paired with the correct IP address.
It plays an important role in helping web browsers translate human-readable domain names into IP addresses that machines can understand. So, whenever you want to visit a site, you don’t have to enter a long number; instead, you type a domain like www.google.com. That way, browsing the internet becomes easier, as you don’t need to remember random numbers before visiting a site.
How Does DNS Work?
Before you can visit a site, you will need to enter a domain name on your web browser. The internet gateway, which is your network provider, sends a lookup request to the DNS server, which inspects the IP address associated with the site.
The DNS server will send the IP back to your network provider, and you will now be able to access the site. Mind you, as long as this process sounds, thanks to caching, it only takes nanoseconds for it to happen.
To have a quicker result, the DNS will save the site’s IP number in its cache for a specific period. That way, if someone wants to visit the site again during this time, the DNS won’t have to start searching for its IP address again, as it has been saved already. This is great because it helps conserve time and the server’s processing power.
Many DNS servers have a cache filled with IP addresses paired with different websites. Sadly, as helpful as this sounds, it has created room for poisoning attacks.
How Does a DNS Poisoning Attack Work?
DNS poisoning attack is also called DNS cache poisoning. It occurs when hackers successfully trick DNS servers into storing the wrong IP addresses in their cache. Let’s use an example to better understand how this works.
Let’s say you want to browse the site “www.domain.com” while connected to your router. Your router then sends a request to the DNS server, and it begins to query other servers to find the IP address linked to this site. This query will get labelled with a numerical identifier like 1100, and the responding server’s reply will have the same marker.

For this poisoning attack to begin, a hacker will bombard the DNS server with many fake responses with different numerical identifiers. All these fake responses trick the DNS into thinking that the requested IP address is part of the hacker’s response. The DNS server will then receive a response with the identifier 1100 and, without suspecting any foul play, will send the hacker’s IP back to your router.
This cyberattack exposes your device to a harmful server filled with malware and puts you at risk of data theft and other online threats. Unfortunately, the DNS will save this fake information in its cache for a while. Anyone who tries to access the site during this period will land on the dangerous site.
What Happens If I Clear My DNS Cache?
If you clear the cache on your device or server, the DNS will start looking for the requested website every time you search for it, as it doesn’t have any saved cache information. However, this won’t keep you completely safe from poisoning attacks, except if the DNS cache isn’t poisoned.
How Can I Detect a DNS Cache Poisoning Attack?
While it’s hard to know when a DNS server gets poisoned, there are still subtle signs you may notice that indicate a poisoning attack has occurred.

If you are browsing on your device and you notice an unexpected redirect, it can indicate cache poisoning. Another signal could be repeatedly observing 404 errors, although it may be a server error and not a deliberate attack.
If you are a DNS server administrator, it’s essential that you stay alert against this attack. One way to tell that the server’s cache has been poisoned is if you notice that users visiting your website keep getting redirected to a specific IP address.
How to Prevent DNS Cache Poisoning
Here are some tips you can practice to protect yourself from any DNS poisoning attack:
- Regularly clean your DNS cache: Waiting until a cache flushes itself means you are letting a poisoned DNS cache exist for weeks. This can put you and many internet users at risk.
- Adopt DNSSEC: A DNS Security Extension (DNSSEC) grants you an additional security layer that eliminates threats like DNS spoofing or cache poisoning. It prevents such attacks by digitally signing on to the data in the DNS server, assuring you that it is valid and from a legitimate source.
- Configure DNS servers using a zero-trust approach: A zero-trust approach requires that every user, software, device, and search request be considered compromised until they get authenticated and validated. This serves as a control point that helps verify the identity of every URL, ensuring that it is not malicious.
- Use DNS Monitoring and Analysis: This method helps track and detect anomalies in your DNS traffic that may indicate a poisoning attack. You can do this using techniques like log analysis, real-time monitoring of DNS server traffic, or packet capture and analysis.
- Use DNS filtering: This method blocks any traffic coming from a malicious IP address or domain. It does this using DNS whitelists or blacklists that get regularly updated with known legitimate or malicious domains.
- Apply Response Rate Limiting (RRL): RRL is a method for reducing the rate at which a DNS server responds to its queries. It helps prevent attacks by reducing the number of responses a single query can generate.
- Implement source authentication: Source authentication is a method for checking the origin of a DNS request to ensure it is legitimate. This process uses tools like TLS and IPsec to identify the requestor and verify that the request was not tampered with during transit.
- Adopt HTTPS for DNS traffic: Using DNS over an HTTP-protected site (DoH) ensures that your DNS traffic remains encrypted and improves privacy by hiding your DNS queries. That means even if a hacker attempts to intercept your traffic, they won’t be able to see the queries you are making or the website you are visiting.
- Select a DoS-resistant DNS resolver: DNS poisoning attacks depend on how fast a DNS server responds, and the response speed is up to the DNS resolver. Getting a fast DNS resolver with an in-built cache poisoning control can help prevent any future attacks.
- Update and patch DNS software: Updating your DNS software regularly can help reduce your device’s exposure to known vulnerabilities, which are the entry point for hackers. So, check if there are new updates or patches from the DNS vendor and use the latest version of the software.
Risks Associated with DNS Cache Poisoning
Listed below are some of the risks that may happen during a poisoning attack:
- Data theft: DNS cache poisoning involves redirecting users to an unexpected web page, most often landing them on a phishing website. This can compromise their sensitive data, like their bank card details and passwords.
- Malware infection: Some of the sites you get redirected to are fraudulent, and attackers use it to infect your device with malware. They can even use automated drive-by downloads that install the malware on your device without you clicking on any link or downloading a file.
- Halting security updates: Cache poisoning can interfere with important security updates, leaving your device vulnerable to dangerous viruses.
DNS Cache Poisoning vs. DNS Spoofing
While most people use these two terms interchangeably, they don’t mean the same thing. DNS spoofing occurs when an attacker bombards the server with many fake or spoofed IP addresses and returns an incorrect query response. This process poisons the cache, which may lead to more DNS spoofing attacks.
In short, DNS cache poisoning occurs due to a spoofing attack.
How Can DNSSEC Help Stop DNS Poisoning Attack?

DNSSEC, short for Domain Name System Security Extensions, is a technology that helps verify the integrity and origin of the data available in a DNS server. DNSSEC helps improve the security of the DNS. It ensures that when you enter a URL, the response you get is accurate, without any changes.
Although few sites use it, it still provides a solution that can help battle poisoning and spoofing attacks using public key cryptography. These cryptographic keys create a digital solution that helps check if the data transmitted comes from a legitimate source.
Nevertheless, till it becomes a standard practice for DNS servers, DNS poisoning attacks remain.
Can a VPN Protect Me from Poisoning Attacks?
A VPN is an essential tool to enhance online security and privacy. ExtremeVPN is your sure bet to escape from any online threat. Our robust security protocols and military-grade AES encryption go an extra length to protect you from any online threat.
So, even if you visit a poisoned site by chance and get directed, you can rest assured that ExtremeVPN will protect your device.
Conclusion
As we try to be safer online, it is important to understand how DNS cache poisoning works and how you can avoid it. This article details how this attack works and includes signs that can help you identify it.
Ensure you update your DNS software to the latest version and follow the preventive measures listed above. You must also use a quality VPN like ExtremeVPN to encrypt your online traffic and keep yourself secure from any threat.